레드라인 먹튀
corporations should concentrate on the dangers that malware such as this can pose and acknowledge the danger of recent phishing assaults.|Based on the takedown discover from European law enforcement, RedLine and Meta ?�are virtually the identical,??an indicator that the two malware strains were being formulated by precisely the same creators. Equally strains were being accessible for sale around the messaging application Telegram.|Thank you for your feed-back. It?�s our objective to deliver the top alternatives personalized to your requirements. We look forward to continuing to guidance your business!|Downloading the scanner opens move-by-stage Recommendations regarding how to use it, even though it's also doable to established it to execute periodic scans for constant defense.|Telegram accounts employed by RedLine and META to market the malware to intrigued purchasers have also been seized, Therefore the sales channels have already been disrupted way too.|These cookies make it possible for us to rely visits and visitors sources so we can easily measure and improve the general performance of our internet site. They help us to be aware of which webpages are one of the most and least preferred and find out how website visitors move throughout the website.|Rudometov has quite a few copyright accounts linked to him underneath numerous faux identities and utilized them to obtain and launder payments received from consumers of your RedLine infostealer.|The complaint is simply an allegation, as well as the defendant is presumed harmless until confirmed guilty beyond a reasonable question in the courtroom of legislation.|PCMag editors decide on and overview solutions independently. If you purchase by way of affiliate hyperlinks, we might make commissions, which assist assistance our testing. Home|Dealing with the Redline Cash and Nicole was so sleek and easy. Essential an individual truthful/transparent that's tough to arrive by Within this industry. Owing to them, I?�m ready to begin my small business and transfer ahead. Surely advocate.|The newly unsealed felony complaint, filed two years in the past within the Western District of Texas, rates Rudometov with entry gadget fraud, conspiracy to commit Laptop or computer intrusion, and income laundering.}
A lot of other providers were being offering me mad delivers, that if I took would have negatively impacted my company. So just desire to thank redline money and Nicole and her group. botnets and stealers.??
Investigators also tracked copyright payments connected to RedLine, uncovering transaction histories and precise account patterns.
Home windows.|The U.S. Division of Justice disclosed that Russian countrywide Maxim Rudometov is indicted more than his suspected involvement in producing and foremost the RedLine malware-as-a-provider Procedure subsequent the dismantling of the data-thieving malware along with the META MaaS System as Section of the international law enforcement effort and hard work Operation Magnus, BleepingComputer stories.|If a business lacks endpoint defense for their employees' gadgets, they ought to strongly take into account utilizing these kinds of an answer to be able to successfully watch gadgets and be certain they aren't compromised.|This staff was really powerful & clear which is difficult to find. I really suggest Redline Funds for business owners who want to proceed increasing. Thank you Nicole.|In the course of Operation Magnus, a coalition of regulation enforcement from 6 nations, coordinated by Eurojust, dismantled RedLine and META by seizing three command servers inside the Netherlands, alongside two domains integral to their operations.|Europol and also the Dutch police also unveiled even further specifics of Operation Magnus on Tuesday, indicating that three servers have been taken offline while in the Netherlands and two domains useful for command and Handle functions by Redline and Meta had been seized.}
From breaking information and in-depth Investigation to rising threats and business traits, our curated information assures you?�re usually educated and well prepared. presence of data files and programs that should not be there?�on person endpoints, which means malware is usually swiftly discovered and taken out once a risk becomes evident.|Mihir Bagwe Bagwe has approximately fifty percent ten years of encounter in reporting on the newest cybersecurity information and developments, and interviewing cybersecurity material specialists.|This takedown has disrupted important revenue channels and eliminated a Major manner of nameless, encrypted communication, thereby restricting the malware's reach and operational versatility.|The infostealer pulls sensitive facts like passwords, login credentials together with other Individually identifiable details from unsuspecting people that were tricked into downloading the malware. |RedLine and META infostealers stole info from an incredible number of victims around the world; U.S. complaint costs developer and administrator; U.S. legislation enforcement seizes infrastructure|23:30 UTC The US governing administration has named and billed a Russian countrywide, Maxim Rudometov, with allegedly developing and administering the infamous Redline infostealer. The Tale of how the FBI found and identified the alleged Russian malware developer spans many years of digital detective perform connecting the suspect's on the internet monikers, email and IP addresses, the iCloud account he reportedly employed for gaming and code sharing, in addition his relationship and social media profiles.|The costs detail his central part in both equally the technical and financial areas of RedLine's operations, building him a important determine from the infrastructure of Among the most commonly deployed infostealer platforms.|Specops Software package?�s report also estimates it stole about 38 million passwords before six months. |Concurrently, stability agency ESET, who in the beginning flagged the infostealer operations towards the Dutch law enforcement, have introduced a 1-time on line scanner for probable victims to check for infections.|IRS-CI special agents are the one federal law enforcement brokers with investigative jurisdiction above violations of The inner Income Code, obtaining a more than a 90 p.c federal conviction fee. The company has 20 subject offices Positioned throughout the U.S. and twelve attaché posts abroad.|U.S. authorities say they were being capable to retrieve data files from Rudometov?�s iCloud account, which includes ??numerous|many|several|quite a few|a lot of|various} data files which were identified by antivirus engines as malware, like at least one that was ??decided to generally be Redline.??The charges have been declared as A part of ??Operation|Procedure} Magnus,??initially unveiled from the Dutch Nationwide Law enforcement on Monday. This decades-in-the-creating operation noticed Global legislation enforcement businesses dismantle the infrastructure of Redline and Meta, two prolific malware strains that were utilized to steal delicate info from numerous persons.|Law enforcement acquired a consider the facts hackers were being thieving from victims and communications that they had with sellers of the RedLine and Meta malware. The identical update could also evidently uncover the hackers??IP address. |Amanda was usually available to help me thru the process regardless of the time of day.she was in a position to get every little thing done within a working day and furnished me with distinctive solutions|Corporations are inspired to assess their cybersecurity profile and figure out whether or not they have the required options and knowhow among their employees to make sure they don't seem to be a target of RedLine attacks.|In a big blow to RedLine and META's operations, Procedure Magnus has properly taken down many Telegram channels used to communicate with affiliate marketers, offer licenses, and assist shoppers of equally infostealers.}
numerous target computers,??based on the Justice Department.|When the U.S. seized two domains as well as the Netherlands together with the identical variety of domains additionally took down 3 servers Employed in the operations, Eurojust, the eu crime coordination agency reported the authorities had detected Nearly 1200 servers connected to these stealers??functions.|If convicted, Rudometov faces a highest penalty of a decade in prison for accessibility machine fraud, five years in prison for conspiracy to dedicate computer intrusion, and twenty years in jail for money laundering.|Worldwide authorities have created the website Procedure Magnus with more means for the public and prospective victims.|Jeffrey G manufactured the expertise really easy and was extremely accessible to support. Funding was fast and I was equipped to get the solutions I wanted from them to aid my small business go on to be successful in the future. Undoubtedly advocate!|Homeowners over the U.S. are now being focused in a sophisticated scam wherein callers pose as mortgage lenders to defraud individuals from countless Countless bucks, the Federal Communications Commission warned Tuesday within a buyer alert. |In conjunction with the disruption work, the Justice Division unsealed prices from Maxim Rudometov, one of the builders and directors of RedLine Infostealer. According to the criticism, Rudometov on a regular basis accessed and managed the infrastructure of RedLine Infostealer, was connected to several copyright accounts accustomed to obtain and launder payments and was in possession of RedLine malware.|International authorities have created a web site at with added sources for the public and likely victims.|Several techniques, together with COVID-19 and Home windows update linked ruses have been used to trick victims into downloading the malware. The malware is advertised available for sale on cybercrime discussion boards and through Telegram channels which provide shopper assist and computer software updates. RedLine and META have contaminated a lot of pcs around the globe and, by some estimates, RedLine has become the best malware variants in the world.|RedLine and META are marketed through a decentralized Malware being a Service (MaaS) design where affiliates purchase a license to make use of the malware, and then launch their own campaigns to contaminate their intended victims. The malware is distributed to victims applying malvertising, e-mail phishing, fraudulent software package downloads, and malicious computer software sideloading.|Continue to, the crackdown is expected to deal a substantial blow to cybercrime. RedLine is Just about the most notorious ??info|information|data|details|facts} thieving??malware plans obtainable inside the hacking planet.|A collaboration Together with the FBI and legislation-enforcement organizations in Europe, the UK, and Australia, Procedure Magnus has seized servers and resource code connected with The 2 malware people, which have stolen facts from millions of victims worldwide.|The stolen qualifications involve Individuals for Web sites like MyPay, the Department of Defense paycheck portal, the U.S. Military?�s Office environment 365 electronic mail ecosystem, and a website owned from the Defense Manpower Knowledge Centre, which serves as being a repository for personal facts including sensitive information regarding a company users??dependents.|The scam artists use threats and coercion to be able to get customers to create a payment for the unproven debt or deliver personal information. They build anxiety for that buyers by threatening to file court motion from them if they don't adjust to their demands inside of forty eight hours, and promising to inform the individuals' businesses and financial institutions about the issue Otherwise fixed.|A federal grand jury from the Northern District of Georgia returned an indictment on Jan. seven charging 3 Russian nationals for his or her involvement in running the copyright mixing providers Blender.io...|RedLine Stealer is a malware-as-a-company (MaaS) platform sold by means of Telegram and on-line hacker boards that targets browsers to collect various facts saved from the person, which includes qualifications and payment card information. It may also have a system inventory to evaluate the attack surface area for further more attacks. }
What's more, it serves being a cautionary tale for would-be cybercriminals regarding the opportunity pitfalls of leaving a long-lasting digital footprint for legislation enforcement to trace ??but a lot more on that in a very minute. for setting up this update. We have been wanting forward to looking at you shortly,??the video claims next to an icon of two palms in handcuffs.|These cookies are necessary for the internet site to function and can't be switched off inside our techniques. They are usually only set in reaction to actions produced by you that amount into a ask for for companies, such as setting your privacy Tastes, logging in or filling in types.|"The Affiliation between moniker GHackiHG and Dendimirror was even further corroborated by info shared on various hacker forums by users bearing each monikers, together with quite a few of which included in their Speak to details: a Skype username acknowledged to law enforcement, the Yandex e-mail deal with, along with a VK profile owned by someone named "?ак?им ??дом??ов (Maxim Rudometov)," in accordance with the grievance.}
Included parties might be notified, and lawful actions are underway.??These results, coupled with Rudometov?�s other on the internet things to do and copyright transfers, cemented his alleged part while in the RedLine operation.|Once the person has downloaded this file, the malware is set up and RedLine will start thieving information and feeding it again to the attacker.}
A web-based Device introduced by cybersecurity firm ESET permits persons to check if their facts was compromised by either RedLine or META. Possible victims are encouraged to:
generally known as ?�logs?�—is marketed on cybercrime discussion boards and useful for further more fraudulent action and other hacks.|Using a powerful password coverage is a good ideal practice to have into the routine of and could make it that Significantly more durable for cybercriminals to compromise a community.|Cybersecurity business ESET, which participated inside the crackdown Procedure as a specialized advisor, produced an internet scanner that can help possible victims ascertain if they are infected by information-stealer malware.|This seizure marks a high-effect go from danger actors relying on well-liked platforms to communicate and coordinate.|Legislation enforcement?�s methods included qualified seizures of domains and servers, halting RedLine and META?�s usage of contaminated equipment. By seizing Telegram channels employed for purchaser support and updates, officials disrupted the malware?�s operational lifeline and hindered its unfold.|For the duration of open period for your Wellbeing Insurance plan Market, You may have witnessed a rise ??maybe a flood ??of adverts for health and fitness plans. The adverts could possibly assure detailed overall health insurance policies??but the|however the|nevertheless the|even so the|although the|though the} system turns out to get confined Added benefits.}
These kind of malware have grown to be especially popular over the underground darkish Net??they are ready-to-use ideal out on the box and provide a robust implies for thieving facts.|Both of those malwares are usually are sold via cybercrime discussion boards and through Telegram channels which offer client support and program updates.|The Procedure 1st announced on Monday ??which also bundled legislation enforcement through the Netherlands, Belgium, Portugal, the United Kingdom, and Australia ??was claimed being a success, as officers declared they have been in possession of ??full|complete|total|entire|whole|comprehensive} obtain??of RedLine and Meta?�s source code, coupled with other infrastructure like license servers and Telegram bots.|Nicole was super enlightening. Extremely challenging to get info in this sector And so the transparency was an enormous earn. Nicole assisted me make the ideal selection for my business enterprise.|America declared expenses currently against Maxim Rudometov, a Russian national, for currently being the suspected developer and administrator of the RedLine malware operation, Among the most prolific infostealers in the last number of years.|In August 2021, regulation enforcement obtained a copy of a portion of the licensing server used by Redline from an unnamed safety organization, and located a treasure trove of data within just server logs that associated with Rudometov's different accounts and companies. This incorporated an IP deal with requesting a Create of RedLine with the licensing server, A further IP handle made use of much more than seven-hundred situations to obtain an iCloud account belonging to Rudometov that contained Redline malware code, a copyright copyright exchange account registered using the Yandex electronic mail tackle, a GitHub account and "a lot of" other inbound links amongst the Russian along with the Redline infostealer.|These infostealers, marketed to cybercriminals and sold via subscriptions, enable attackers to steal credentials and economic information and bypass multi-factor authentication.|These ?�logs??of stolen knowledge are offered on cybercrime discussion boards, giving hackers a valuable trove to use even more. Security industry experts Observe RedLine?�s notoriety on account of its ability to infiltrate even probably the most protected corporate networks, boosting alarms across industries.|Providing incentives for critiques or requesting them selectively can bias the TrustScore, which fits against our guidelines.|The authorities had been led into the Main A part of the infrastructure after getting ideas from ESET, mapping an in depth community of over 1,200 servers located in various nations, which communicated Along with the central servers during the Netherlands.|"Rudometov regularly accessed and managed the infrastructure of RedLine Infostealer, was connected to different copyright accounts utilized to acquire and launder payments, and was in possession of RedLine malware," reads the announcement from the DOJ.|Or it?�s a health care discount card and never insurance plan whatsoever. Some advertisements could assure rewards or rebates to anyone who indicators up for your strategy. Or they may say they?�re from The federal government ??or governing administration-endorsed, hoping to gain your have faith in. How for making heads or tails of everything?|Authorities finally gathered sufferer log data stolen from computers infected with RedLine and Meta, determining many unique usernames and passwords, in addition to e-mail addresses, bank accounts, copyright addresses, and credit card numbers that have been stolen by various malware operators.|How to protect your individual information and facts and privateness, continue to be Harmless on line, and aid your Young ones do the same.|Change passwords on your internet shopping accounts in the event they had been compromised. When the package arrived from Amazon or One more on the internet marketplace, mail the System a information so they can look into taking away the seller.|The stealers are accountable for the theft of millions of one of a kind qualifications from Intercontinental victims, authorities explained.|The complaint disclosed that Redline had been used to contaminate countless personal computers around the globe because February 2020, together with ??several|a number of|numerous|many|various|quite a few} hundred??devices employed by the U.S. Division of Protection. It?�s not however recognised if Rudometov has become arrested. If convicted, he faces up to 35 yrs in prison.}
Scammers are sending people today fake ??luxury??items like rings, attractiveness solutions, as well as Bluetooth speakers. This is usually identified as a ?�brushing scam,??so called since it?�s ?�brushing up????or growing ??the scammer?�s product sales.|What may very well be much better than opening the mailbox or maybe the entrance doorway and finding an sudden offer? Totally free gifts might seem like enjoyable ??but when an surprising bundle lands with your doorstep, it might include a greater Expense than you anticipated.|How a series of opsec failures led US authorities towards the alleged developer of your Redline password-thieving malware|Customers filing BBB problems have been given cellular phone phone calls from fraudulent men and women proclaiming to get a group agency seeking to accumulate a credit card debt. Shoppers have asked for validation of the personal debt, however the company has refused to provide this information and facts.|Nicole & her group were extremely useful. Redline Funds assists you discover a terrific selection of funding selections for your small business and her crew is very trustworthy. I extremely endorse them.|These email messages will typically be based upon one thing like present-day functions??often|frequently|usually|typically|generally|normally} the COVID pandemic or some other celebration which will be applicable to a large number of persons.|Email messages of this type will try to steer the person to adhere to a URL backlink which will acquire them to a malicious Web page.|Rudometov continues to be billed with obtain gadget fraud, conspiracy to commit Computer system intrusion, and money laundering.|Employing MFA enormously boundaries the success of stolen credentials and in many situations will stop a cybercriminal in his tracks, whether or not they may have a plain-text password at hand.|Make sensible browsing decisions, know your legal rights, and clear up problems whenever you shop or donate to charity.|We use committed people today and intelligent technological innovation to safeguard our platform. Discover how we battle faux testimonials.|Being a issue of policy, BBB will not endorse any item, support or organization. Companies are less than no obligation to seek BBB accreditation, plus some corporations will not be accredited because they haven't sought BBB accreditation.|Rudometov faces the next rates for his involvement and foremost purpose inside the RedLine infostealer Procedure.|Thanks to their prevalent availability, each stealers are actually used by risk actors with several amounts of sophistication. Innovative actors have distributed the stealers being an Preliminary vector on which to conduct even more nefarious activity, which include providing ransomware, while unsophisticated actors have applied one or the opposite from the stealers for getting to the cybercriminal game to steal qualifications.|The unsealed costs together with the extra detainment of two unnamed people today by Dutch National Law enforcement, are the latest to come back outside of Operation Magnus, a world legislation enforcement Procedure geared toward halting the infamous RedLine and Meta infostealers. |Safety scientists at Specops Software program not long ago believed that RedLine infections experienced stolen around 170 million passwords in past times 6 months. }
Working with security consciousness teaching is a crucial action in making sure safety from negative actors. Cybercriminals run over a regulation-of-averages method, which means they are aware that when they send a particular range of phishing e-mail, they're able to assume a minimum amount variety of close end users to fall target to them.
E-mail filters are necessary in stopping the mass of phishing attacks that happen on a daily basis. These filters can identify incoming email messages that contain malware or destructive URLs and may isolate and prevent them from remaining accessed by consumers as though they have been ordinary. Magnus??that took down considered one of the greatest infostealer operations across the world was a chance to keep track of down the alleged handler on the RedLine infostealer Procedure, which contaminated hundreds of techniques utilized by the United States Office of Defense customers.|Two people today ended up also arrested in Belgium, with a single previously staying produced and the other said to become a buyer of your malware functions.|In line with details posted in community area, the employee?�s entry was utilized to acquire, and subsequently leak, restricted resource code owned through the tech organization.|While the Dutch police took down a few servers and its Belgian counterparts seized a number of interaction channels linked to the Redline and Meta infostealers, the U.S. Division of Justice on Monday unsealed rates towards Most likely one of many most important handlers from the operations.|Yandex is usually a Russian communications company, and subsequent investigation connected this e mail handle to other monikers which includes "GHackiHG" linked to Dendimirror, moreover Google and Apple products and services used by Rudometov along with a courting profile.|?�Who cares whenever they generate a phony overview in my identify???you might say. Nicely, if you got a bundle you didn?�t buy, this means anyone likely has your personal info ??and undoing the likely damage from identification theft could cost you time and cash.|These cookies enable the website to supply enhanced functionality and personalization. They may be set by us or by 3rd party vendors whose products and services we have included to our internet pages. If you don't make it possible for these cookies, some or these products and services may well not purpose appropriately.|Presented the moniker "Inexperienced Mirage," Individuals powering the phone calls usually threaten foreclosure, then supply aid In the event the victims mail payments by way of atypical routes.|America doesn't believe that it's in possession of the many stolen data and carries on to research.|Anyone can compose a copyright evaluate. Individuals who publish assessments have ownership to edit or delete them at any time, and so they?�ll be shown provided that an account is Energetic.|To that conclusion, RedLine can also perform other malicious features, for example uploading and downloading documents, and executing instructions. Meta In the meantime is largely a clone of RedLine that performs similar functions as well as operates by means of an MaaS design.|Jeff did a terrific career encouraging get funding for my business. It was couple of hurdles in the course of the method but Jeff?�s effort and resolve authorized us to receive the proper offer. Thanks once again. Mr. Garcia was excellent to work with.|The site is protected. The https:// makes sure that you'll be connecting to your Formal Site and that any information you provide is encrypted and transmitted securely.|If uncovered responsible, Rudometov faces approximately 10 years in jail for entry device fraud, 5 years for conspiracy to commit Pc intrusion, and twenty years for dollars laundering, based on the press launch.|Eco-friendly Mirage scammers have impersonated greater than four hundred house loan institutions and prompted many 1000s of dollars of losses to deceived homeowners, lots of whom only find out of the fraud when their precise lender begins foreclosure proceedings, the FCC said.}}
 Ariana Richards Then & Now!
Ariana Richards Then & Now! Ashley Johnson Then & Now!
Ashley Johnson Then & Now!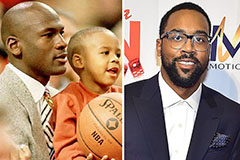 Marcus Jordan Then & Now!
Marcus Jordan Then & Now!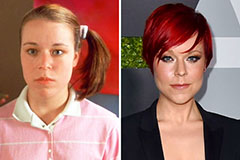 Tina Majorino Then & Now!
Tina Majorino Then & Now! Nicholle Tom Then & Now!
Nicholle Tom Then & Now!